ISO 27001 Consultancy
ISO 27001:2013
INFORMATION SECURITY MANAGEMENT SYSTEM (ISMS)

IT systems have evolved to the point where they can process a large amount of data in a short amount of time. At the same time, protecting them is growing more difficult. Information must be kept secure and accessible, and its integrity must be preserved, in order to enable safe processing. After all, if information begins to leak, it can lead to a trust issue and a competitive disadvantage.
Information security is becoming increasingly vital, especially in the age of Facebook, Twitter, and other social media platforms, but it is also becoming increasingly vulnerable to dangers. As a result, well-organized and clearly operational professional IT security management has become a critical requirement for businesses.
We provide you with an independent review of the degree of consistency of your information security management system (ISMS) to the ISO 27001 requirements with an ISO 27001 certification.
We examine the security of information and IT environments using ISO 27001, a globally recognized standard. It outlines the implementation requirements as well as the documentation for an ISMS. Security risks can be reduced, and IT security processes can be implemented to help you improve the quality of your systems over time.
The Requirement for ISO 27001:2013
the standard uses a risk management process to preserves the confidentiality, integrity and availability of information, giving confidence to relevant interested parties that risks are adequately managed.Actions to address the risks includes policies, procedures and technology controls.
The following are the ISMS requirements:
Organizational context
Defining the standard's intended scope in an organization, as well as requirements for external and internal concerns and interested parties. Understanding the company and its context, as well as the expectations of stakeholders and the scope of management systems, can help with this.
Leadership
Defining top management tasks, high-level information security policy content, and roles and responsibilities. This can be accomplished through getting top management support for a successful ISMS and security policy, as well as explicitly creating security roles and duties.
Planning
Define the information security objectives, risk assessment requirements, risk treatment requirements, and Statement of Applicability requirements. Setting a plan for how to attain goals and taking measures to address risks and opportunities within the organization are two ways to identify information security objectives.
Support
Defining needs for availability of resources, competencies, awareness, communication, and management of papers and records by providing the appropriate resources, communications, and training.
Operation
Determining how risk assessment and treatment, as well as controls and other processes, will be implemented to meet information security goals. This can be accomplished by using a risk-based approach to the assessment, identifying the risk and possible treatments, building a risk treatment plan, and putting it into action on the identified risks.
Monitoring, measurement, analysis, evaluation, internal audit, and management review
Defining requirements for monitoring, measurement, analysis, evaluation, internal audit, and management review.
Improvement
Defining standards for nonconformities, corrections, corrective measures, and continuous improvement by seizing chances to make security procedures and controls more effective.
All about ISO/IEC 27001:2013
Who: ISO/IEC 27001:2013 is reasonable for an association that needs to further develop their data security the board framework utilizing the broadly known data security driving practices standard and gets the obligatory security affirmation.
When: An association can execute and get guaranteed on ISO/IEC 27001:2013 whenever, yet it isn’t obligatory. The association might decide to carry out the standard first and get guaranteed some other time when the association is constrained by guidelines or when the association needs to expand trust among clients and customers, giving broadened security confirmation.
Where: The standard can be taken on and carried out in any association paying little mind to its size, type, nature, private or state claimed, benefit or non benefit.
Why: ISO/IEC 27001:2013 will help associations by carrying out security in an extensive way. It assists associations with consenting to lawful prerequisites, accomplish advertising advantage by consoling clients about security, lower costs by forestalling occurrences, and be better coordinated by characterizing cycles and methods for a planned way to deal with data security.
How: An organization that wants to improve its security management system using ISO/IEC 27001:2013 as its standard would undergo the following activities: Gap analysis, Remediation, Measure, Monitor and Review, Internal audit and Certification .
FAQ
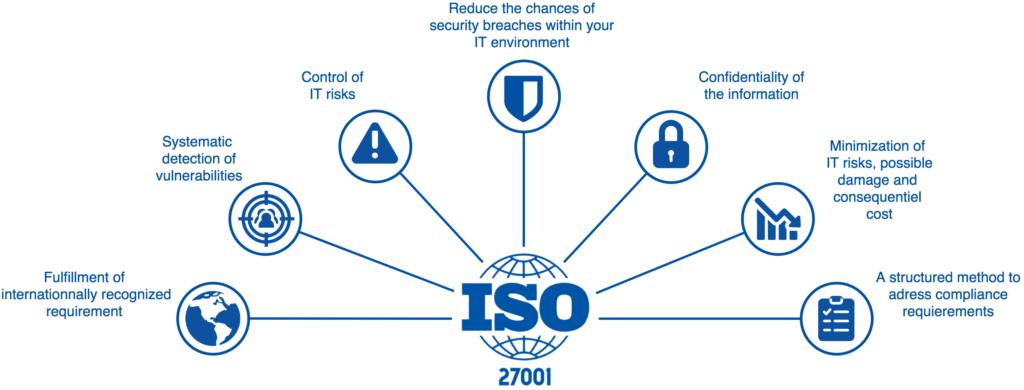
ISO 27001 is a management system for protecting information that is consistent and centrally regulated. Furthermore, efficient monitoring and control of IT security hazards reduces dangers to all company processes.
You’ll be defending your company from cyber-attacks, data loss, and the resulting financial and reputational damage. Legal safeguards are in place, and hacker attacks are minimized, as well as the hacker’s capacity to access critical information. Other benefits of ISO 27001 certification include:
- Assured availability of your IT systems and processes
- Confidentiality of your information
- Competitive advantage
- Minimization of IT risks and potential damages
- Exposure and elimination of weak areas · Control of IT risks
- Guaranteed satisfaction of compliance requirements
- Cost reduction
Your certificate has a three-year validity period. Your continuous improvement process can be secured thanks to the annual surveillance audit and recertification before three years have passed.
Organizations are required to equip their networks according to minimum standards. In addition, technical and organizational provisions need to be met to ensure the availability, integrity, authenticity and confidentiality of data. Hacker attacks must be reported immediately.
Funding available up to 70%
(new supplementary budget announcement: Enhanced EDG till March 2023)
To help companies adopt internationally-recognised standards and certifications in key industries, as well as in new and emerging sectors. By doing so, your company should achieve outcomes, such as increased business competitiveness locally and internationally, enhanced market access, and/ or increased trust in your products and services.
Scope of work covers:
- Assessment and adoption of relevant standards for business growth
What is not covered:
- Cost of annual surveillance or recertification of current standards which the company is already certified to
- Standards referred to in local regulatory acts
- Product testing and validation of existing or off-the-shelf products
- Basic standards such as ISO 9001, ISO 14001 and ISO 45001
Support level:
- SMEs up to 70%; non-SMEs up to 50% of qualified costs from 1 April 2022 to 31 March 2023
- Certification fees are a supportable cost component

